Timeline: Jan’22 – Feb’23
At Secureworks, I tackled high customer churn on the Taegis VDR SaaS platform, where churn rates reached 50%. As Principal Product Designer, I led the end-to-end design of critical features including batch actions, SSO authentication, and customizable asset scanning—empowering users to streamline workflows and prioritize vulnerabilities more effectively. These improvements reduced churn to 30%, re-engaged inactive users, and strengthened customer trust. Ultimately, my work elevated the platform’s usability and contributed to a more intuitive and efficient user experience.
Intro
Secureworks (previously owned by Dell Technologies and recently acquired by Sophos) offers a vulnerability scanning and remediation self-serve application called Taegis VDR (Vulnerability Detection and Response). VDR’s primary use case is to continuously discover and scan network assets to identify security-related vulnerabilities. These vulnerabilities are then prioritized using machine learning algorithms to assist vulnerability analysts (primary users) in remediating the most critical ones more quickly.
My role
Principal Product Designer
I spearheaded multiple customer-centric initiatives by collaborating closely with product managers and tech leads to identify and address key user pain points, resulting in a significant reduction in customer churn. Additionally, I partnered with a UX researcher and UI/Engineering Lead on long-term projects, including strategic research to uncover new opportunities and aligning the existing user interface with established design system patterns and components for improved consistency and usability.
Some of the features I worked on include batch actions, user authentication using SSO, intelligence feed, and gap audit to align the UI with the design system, among others.
I also designed the user experience for a feature that allowed users to customize asset scanning based on specific rules. This feature helped customers avoid involuntary asset shutdowns, particularly for critical assets, ultimately aiding the company in regaining customers’ trust in the product.
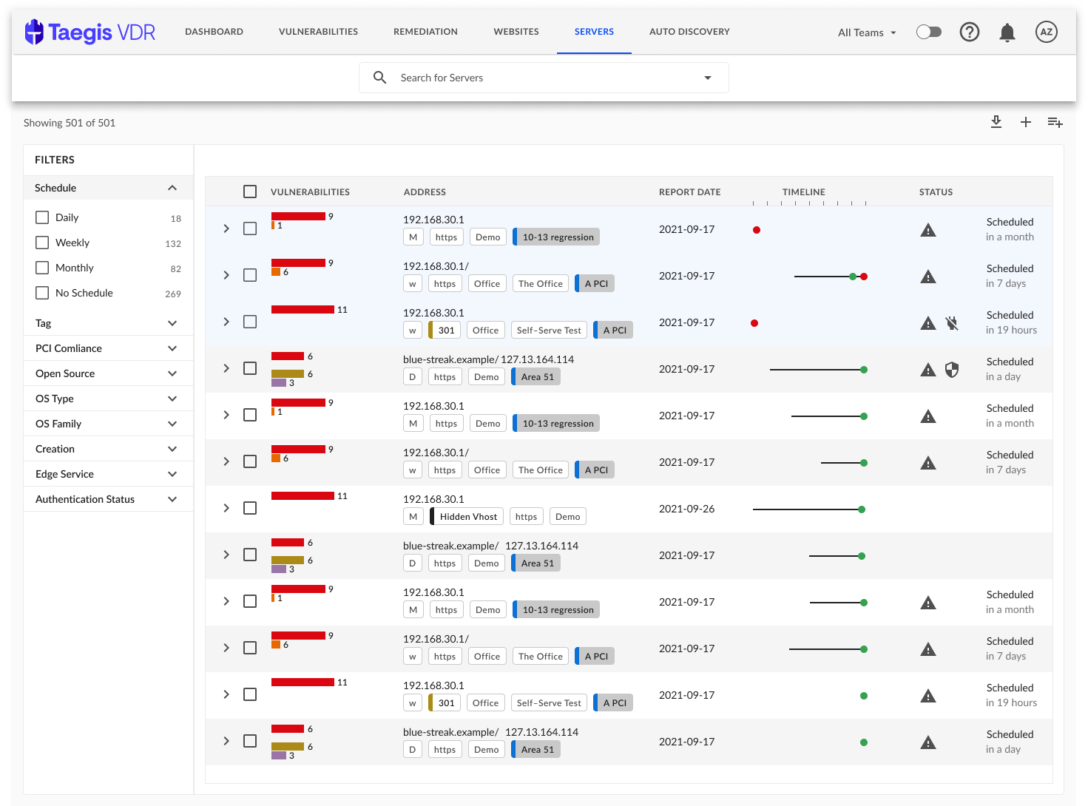
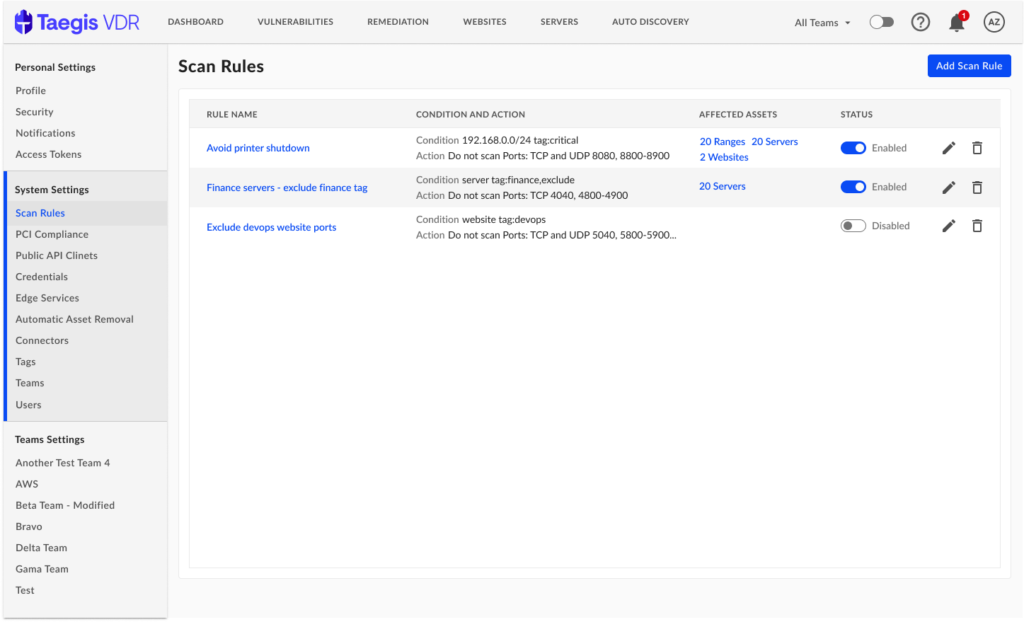
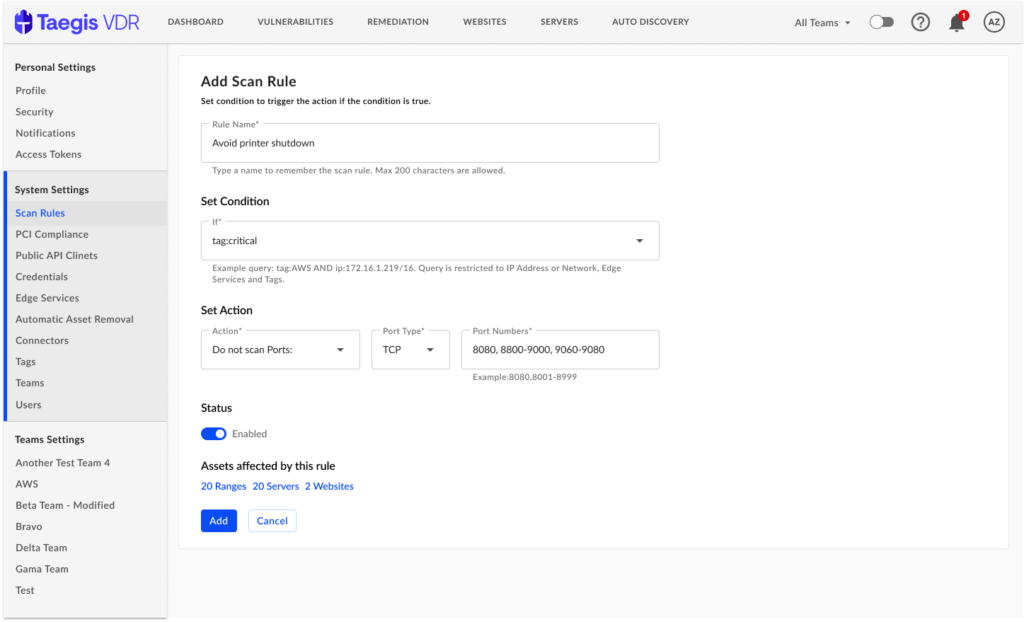
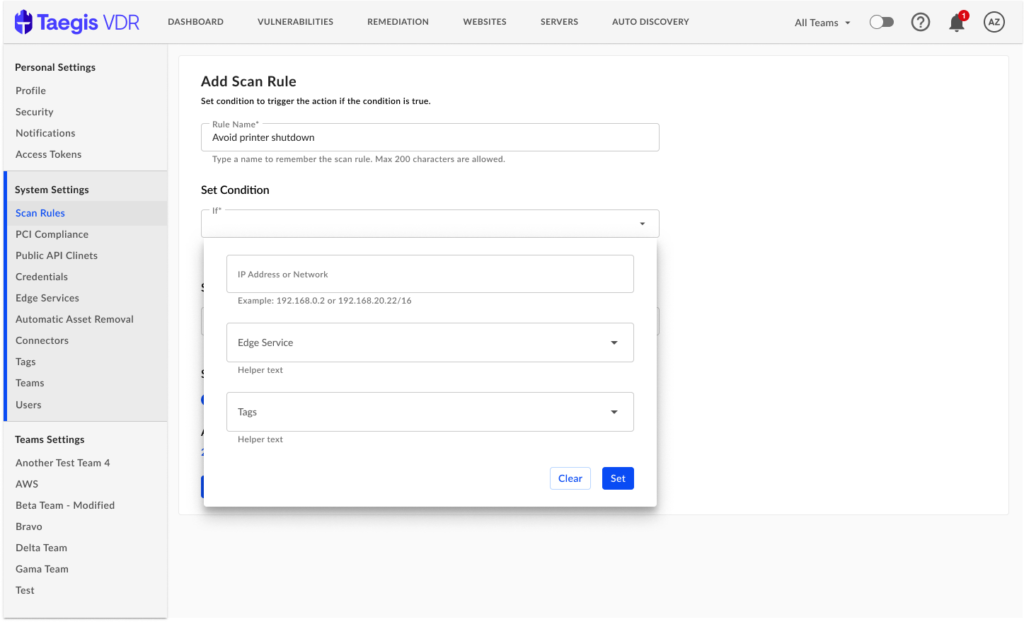
Scan Rules
Product documentation notes: https://docs.ctpx.secureworks.com/vdr/userGuide/generalUse/scan_rules/
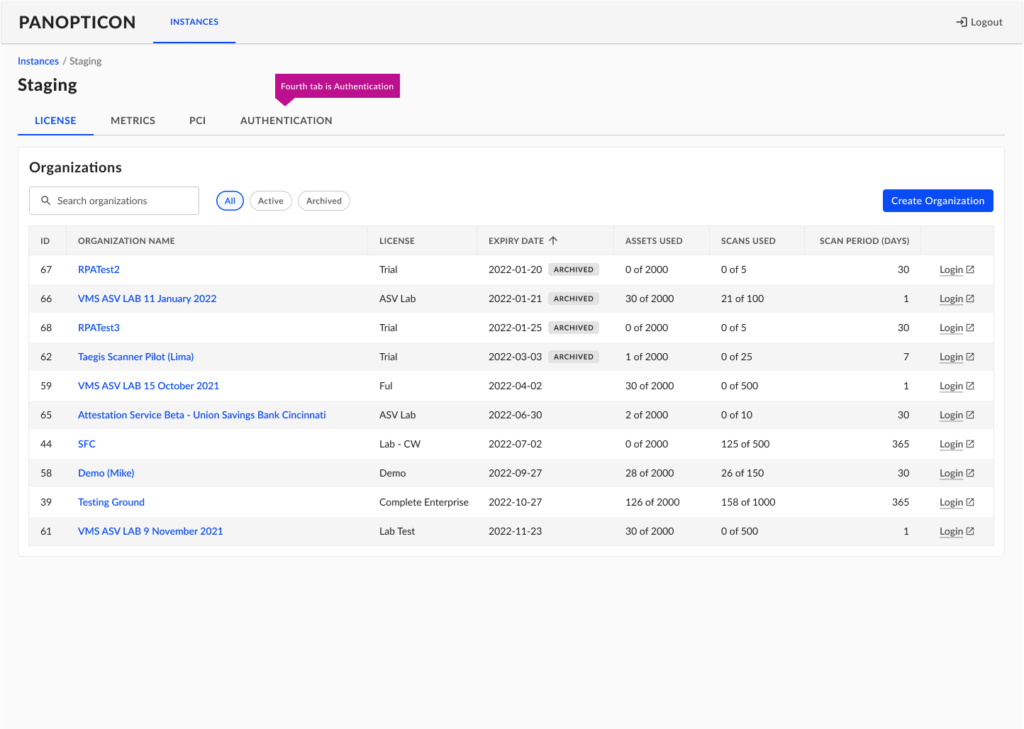
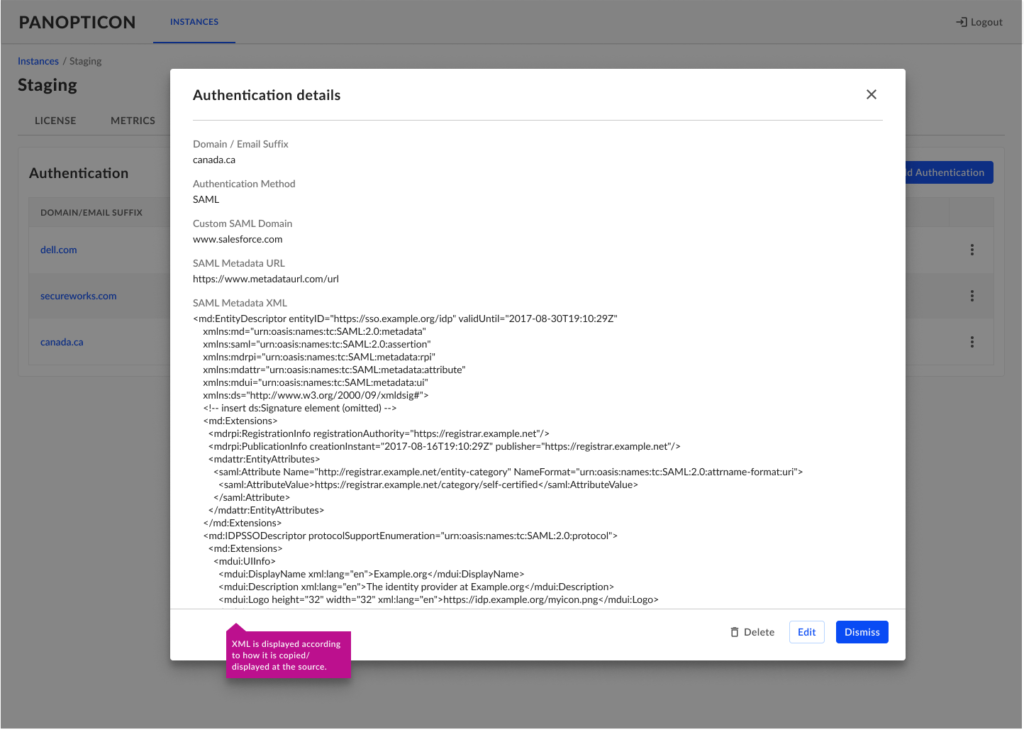
User Authentication/SSO
VDR’s tenant management portal: Authentication (SSO) management module.
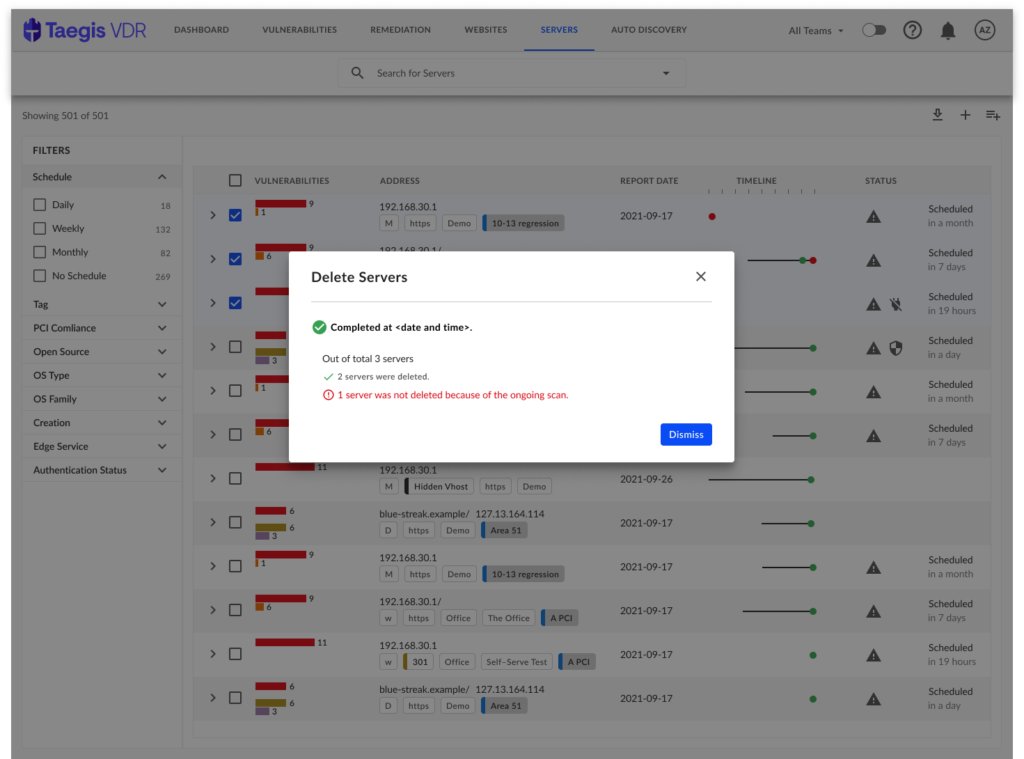
Batch Actions Pattern
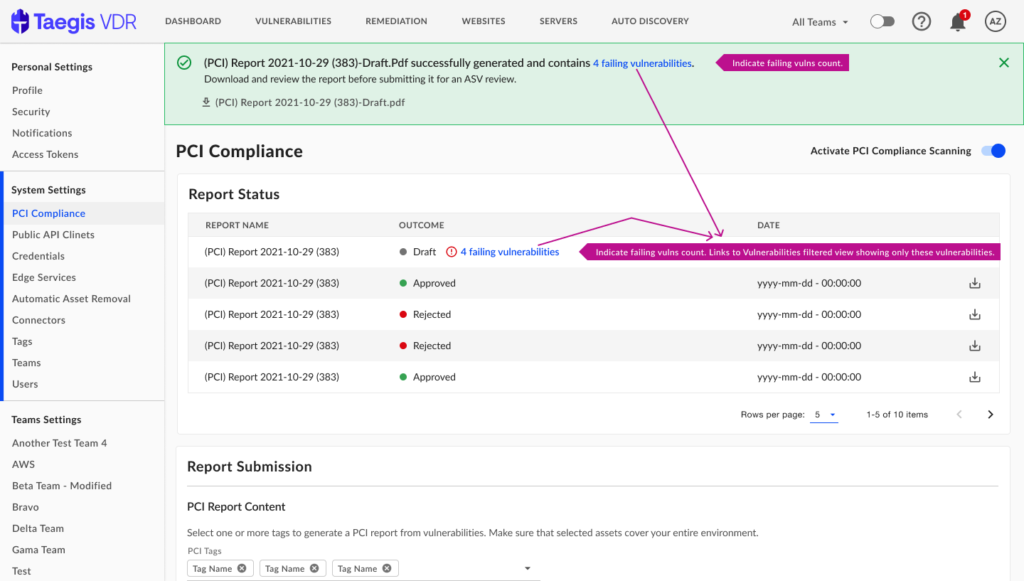
Payment Card Industry (PCI) compliance UX enhancements
User problems
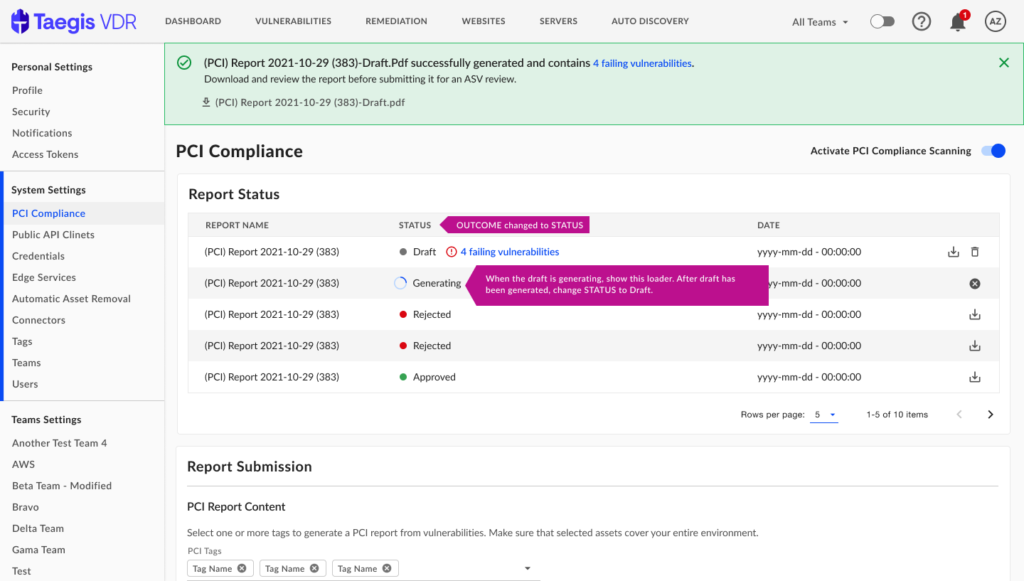
Discoverability: Users often rely on the old workflow to mark vulnerabilities as false positives and may overlook the need to submit those tagged for PCI review to an Approved Scanning Vendor (ASV) after marking them as false positives.
Failing to promptly resolve false positive vulnerabilities may lead to non-compliance with PCI standards. PCI compliance is periodically assessed, and if users spend significant time marking vulnerabilities as false positives without ensuring their resolution, they may inadvertently remain non-compliant. Consequently, they may submit a compliance report believing everything is in order, only to discover later that they are still non-compliant. This can result in missed deadlines and insufficient time to address all failing vulnerabilities before the next assessment.
To solve for the issue, following was proposed and implemented:
1. Display a warning message to inform user that vulnerabilities that are marked as false positive need to be reviewed by an ASV.
2. Show count of failing vulnerabilities on the success message after PCI report is generated.
3. Indicate failing vulnerabilities count on the table where generated reports are displayed.
4. Show warning when user is submitting the ASV report.
5. Future enhancement: For individual vulnerabilities that are marked as FP, give an option to comment and submit to ASV on the form itself.
Outcomes
By releasing the Scan Rules feature alongside impactful user experience enhancements in VDR, we achieved a notable quarterly decrease in churn from over 50% to 30%. Additionally, we successfully re-engaged some previously inactive customers, effectively restoring their confidence in the product and revitalizing their usage of VDR.